链路备份的IPSec VPN和设备备份的IPSec VPN:
首先实验的是链路备份的 IPSec VPN,下面是实验拓扑: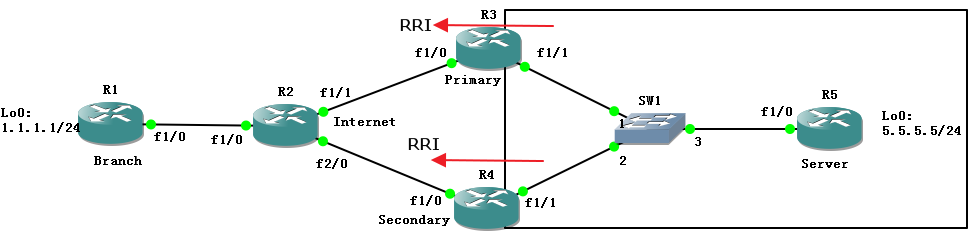
IP地址配置:
R1(Branch):
Branch(config-if)#ip add 12.1.1.1 255.255.255.0
Branch(config-if)#no shu
Branch(config-if)#int lo0
Branch(config-if)#ip add 1.1.1.1 255.255.255.0
Branch#conf t
Branch(config)#ip route 0.0.0.0 0.0.0.0 12.1.1.2
R2(Internet):
R2(config)#int f1/0
R2(config-if)#ip add 12.1.1.2 255.255.255.0
R2(config-if)#no shu
R2(config)#int f1/1
R2(config-if)#ip add 23.1.1.2 255.255.255.0
R2(config-if)#no shu
R2(config-if)#int f2/0
R2(config-if)#ip add 24.1.1.2 255.255.255.0
R2(config-if)#no shu
R2(config-if)#int lo0
R2(config-if)#ip add 2.2.2.2 255.255.255.0
R3(Primary):
R3(config)#int f1/0
R3(config-if)#ip add 23.1.1.3 255.255.255.0
R3(config-if)#no shu
R3(config-if)#int f1/1
R3(config-if)#ip add 10.1.1.3 255.255.255.0
R3(config-if)#no shu
R3(config-if)#int l0
R3(config-if)#ip add 3.3.3.3 255.255.255.0
R3(config-if)#end
R3(config)#router os 1
R3(config-router)#router-id 3.3.3.3
R3(config-router)#net 10.1.1.0 0.0.0.255 a 0
Primary(config)#ip route 0.0.0.0 0.0.0.0 23.1.1.2
R4(Secondary):
R4(config)#int f1/0
R4(config-if)#ip add 24.1.1.4 255.255.255.0
R4(config-if)#no shu
R4(config-if)#int f1/1
R4(config-if)#ip add 10.1.1.4 255.255.255.0
R4(config-if)#no shu
R4(config-if)#int l0
R4(config-if)#ip add 4.4.4.4 255.255.255.0
R4(config-if)#router os 1
R4(config-router)#router-id 4.4.4.4
R4(config-router)#net 10.1.1.0 0.0.0.255 a 0
R4(config)#ip route 0.0.0.0 0.0.0.0 24.1.1.2
R5(Server):
R5(config)#int f1/0
R5(config-if)#ip add 10.1.1.5 255.255.255.0
R5(config-if)#no shu
R5(config-if)#int l0
R5(config-if)#ip add 5.5.5.5 255.255.255.0
R5(config-if)#router os 1
R5(config-router)#router-id 5.5.5.5
R5(config-router)#net 0.0.0.0 255.255.255.255 a 0
链路备份的IPSec VPN配置:
Branch(config)#crypto is po 10
Branch(config-isakmp)#authentication pre-share
Branch(config-isakmp)#exi
Branch(config)#crypto isakmp key 0 cisco address 23.1.1.3
Branch(config)#crypto isakmp key 0 cisco address 24.1.1.4 //密钥可以不一样
Branch(config)#crypto isakmp keepalive 10 periodic //启用DPD
Branch(config)#ip access-list extended vpn
Branch(config-ext-nacl)#permit ip 1.1.1.0 0.0.0.255 5.5.5.0 0.0.0.255
Branch(config-ext-nacl)#exi
Branch(config)#crypto ipsec transform-set trans esp-des esp-md5-hmac
Branch(cfg-crypto-trans)#exi
Branch(config)#crypto map cisco 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
Branch(config-crypto-map)#match address vpn
Branch(config-crypto-map)#set peer 23.1.1.3 //先配置23.1.1.3为主用网关,后配置的24.1.1.4为备用的网关
Branch(config-crypto-map)#set peer 24.1.1.4
Branch(config-crypto-map)#set transform-set trans
Branch(config-crypto-map)#int f1/0
Branch(config-if)#crypto map cisco
Primary(config)#crypto isakmp po 10
Primary(config-isakmp)#au pre-share
Primary(config-isakmp)#exi
Primary(config)#crypto isakmp key 0 cisco address 12.1.1.1
Primary(config)#crypto isakmp keepalive 10 periodic //开启DPD
Primary(config)#ip access-list extended vpn
Primary(config-ext-nacl)#permit ip 5.5.5.0 0.0.0.255 1.1.1.0 0.0.0.255
Primary(config-ext-nacl)#exi
Primary(config)#crypto ipsec transform-set trans esp-des esp-md5-hmac
Primary(cfg-crypto-trans)#exi
Primary(config)#crypto map cisco 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
Primary(config-crypto-map)#match address vpn
Primary(config-crypto-map)#set peer 12.1.1.1
Primary(config-crypto-map)#set transform-set trans
Primary(config-crypto-map)#reverse-route
Primary(config-crypto-map)#set reverse-route tag 10//启用RRI,并解决回包问题
This will remove previously installed VPN routes and SAs
Primary(config-crypto-map)#int f1/0
Primary(config-if)#crypto map cisco
*Apr 23 14:15:21.343: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
Primary(config-if)#router os 1
Primary(config-router)#redistribute static route-map RRI subnets
Primary(config-router)#exi
Primary(config)#route-map RR1
Primary(config-route-map)#match tag 10
Primary(config-route-map)#exi
Secondary(config)#crypto isakmp po 10
Secondary(config-isakmp)#authentication pre-share
Secondary(config)#crypto isakmp key 0 cisco address 12.1.1.1
Secondary(config)#exi
Secondary(config)#ip access-list extended vpn
Secondary(config-ext-nacl)#permit ip 5.5.5.0 0.0.0.255 1.1.1.0 0.0.0.255
Secondary(config-ext-nacl)#exi
Secondary(config)#crypto isakmp keepalive 10 periodic
Secondary(config)#crypto ipsec transform-set trans esp-des esp-md5-hmac
Secondary(cfg-crypto-trans)#exi
Secondary(config)#crypto map cisco 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
Secondary(config-crypto-map)#match address vpn
Secondary(config-crypto-map)#set peer 12.1.1.1
Secondary(config-crypto-map)#set transform-set trans
Secondary(config-crypto-map)#reverse-route
Secondary(config-crypto-map)#set reverse-route tag 10
This will remove previously installed VPN routes and SAs
Secondary(config-crypto-map)#int f1/0
Secondary(config-if)#crypto map cisco
*Apr 23 14:17:47.915: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
Secondary(config-if)#router os 1
Secondary(config-router)#redistribute static subnets route-map RRI
Secondary(config-router)#exi
Secondary(config)#route-map RRI
Secondary(config-route-map)#match tag 10
Secondary(config-route-map)#exi
Primary(config)#int f1/0
Primary(config-if)#shu
Secondary#sho crypto en connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec DES+MD5 0 26 31 24.1.1.4
2 IPsec DES+MD5 26 0 0 24.1.1.4
1001 IKE SHA+DES 0 0 0 24.1.1.4
这里说一下,当Primary这边的接口down了的话,随着安全关联的消失,反向注入产生的路由也跟随者消失了。还有,链路备份的高可用性IPSec VPN是不支持抢占的。
Server#sho ip ro ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is not set
1.0.0.0/24 is subnetted, 1 subnets
O E2 1.1.1.0 [110/20] via 10.1.1.4, 00:01:22, FastEthernet1/0
现在来做一下设备的备份,设备备份的IPSec VPN(Redundancy VPN):
redundancy VPN主要是使用HSRP来提供设备级别的备份,实验拓扑如下: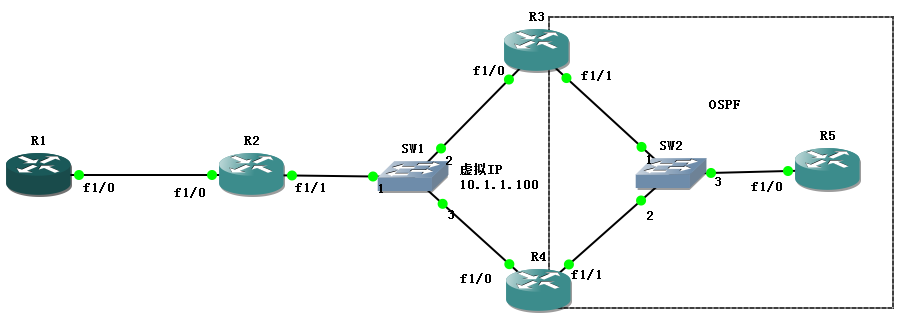
设备IP地址配置:
R1:
interface Loopback0
ip address 1.1.1.1 255.255.255.0
interface FastEthernet1/0
ip address 12.1.1.1 255.255.255.0
duplex auto
speed auto
crypto map cisco
!
ip route 0.0.0.0 0.0.0.0 12.1.1.2
R2:
interface Loopback0
ip address 2.2.2.2 255.255.255.0
!
interface FastEthernet1/0
ip address 12.1.1.2 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/1
ip address 10.1.1.2 255.255.255.0
duplex auto
speed auto
R3:
interface Loopback0
ip address 3.3.3.3 255.255.255.0
!
interface FastEthernet1/0
ip address 10.1.1.3 255.255.255.0
duplex auto
speed auto
standby 1 ip 10.1.1.100
standby 1 priority 105
standby 1 preempt
standby 1 name cisco
crypto map cisco redundancy cisco
!
!
interface FastEthernet1/1
ip address 20.1.1.3 255.255.255.0
duplex auto
speed auto
!
!
router ospf 1
router-id 3.3.3.3
log-adjacency-changes
redistribute static subnets route-map RRI
network 20.1.1.0 0.0.0.255 area 0
!
ip route 0.0.0.0 0.0.0.0 10.1.1.2
!
ip access-list extended vpn
permit ip 5.5.5.0 0.0.0.255 1.1.1.0 0.0.0.255
!
route-map RRI permit 10
match tag 10
R4
interface Loopback0
ip address 4.4.4.4 255.255.255.0
!
interface FastEthernet1/0
ip address 10.1.1.4 255.255.255.0
duplex auto
speed auto
standby 1 ip 10.1.1.100
standby 1 preempt
standby 1 name cisco
crypto map cisco
!
!
interface FastEthernet1/1
ip address 20.1.1.4 255.255.255.0
duplex auto
speed auto
!
!
router ospf 1
router-id 4.4.4.4
log-adjacency-changes
redistribute static subnets route-map RRI
network 20.1.1.0 0.0.0.255 area 0
ip route 0.0.0.0 0.0.0.0 10.1.1.2
!
route-map RRI permit 10
match tag 10
interface Loopback0
ip address 5.5.5.5 255.255.255.0
!
interface FastEthernet1/0
ip address 20.1.1.5 255.255.255.0
duplex auto
speed auto
!
router ospf 1
router-id 5.5.5.5
log-adjacency-changes
network 5.5.5.0 0.0.0.255 area 0
network 20.1.1.0 0.0.0.255 area 0
HSRP配置:
R3:
interface FastEthernet1/0
ip address 10.1.1.3 255.255.255.0
duplex auto
speed auto
standby 1 ip 10.1.1.100
standby 1 priority 105
standby 1 preempt
standby 1 name cisco
R4:
interface FastEthernet1/0
ip address 10.1.1.4 255.255.255.0
duplex auto
speed auto
standby 1 ip 10.1.1.100
standby 1 preempt
standby 1 name cisco
crypto map cisco
IPSec VPN配置:
R1:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 10.1.1.100
crypto isakmp keepalive 10 periodic
!
!
crypto ipsec transform-set trans esp-des esp-md5-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 10.1.1.100
set transform-set trans
match address vpn
!
ip access-list extended vpn
permit ip 1.1.1.0 0.0.0.255 5.5.5.0 0.0.0.255
!
R3:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 12.1.1.1
crypto isakmp keepalive 10 periodic
!
!
crypto ipsec transform-set trans esp-des esp-md5-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 12.1.1.1
set transform-set trans
set reverse-route tag 10
match address vpn
reverse-route static //若没有这个关键字,必须要有IPSec SA才会产生反向路由,主要,active路由器才会产生反向路由
interface FastEthernet1/0
crypto map cisco redundancy cisco //只用redundancy关键字调用HSRP的名字,哪台为活动的路由器就会使用虚拟IP和远端的peer建立IPSec VPN
ip access-list extended vpn
permit ip 5.5.5.0 0.0.0.255 1.1.1.0 0.0.0.255
!
Redundancy VPN是支持抢占的,因为HSRP支持抢占(当然前提是要开启preempt)
R4:
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 12.1.1.1
crypto isakmp keepalive 10 periodic
!
!
crypto ipsec transform-set trans esp-des esp-md5-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 12.1.1.1
set transform-set trans
set reverse-route tag 10
match address vpn
reverse-route static
interface FastEthernet1/0
crypto map cisco redundancy cisco
ip access-list extended vpn
permit ip 5.5.5.0 0.0.0.255 1.1.1.0 0.0.0.255
R1#ping 5.5.5.5 so 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!.!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 288/523/748 ms
R3#sho cry en conn active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec DES+MD5 0 5 5 10.1.1.100
2 IPsec DES+MD5 5 0 0 10.1.1.100
1001 IKE SHA+DES 0 0 0 10.1.1.100
R5#sho ip ro ospf
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is not set
1.0.0.0/24 is subnetted, 1 subnets
O E2 1.1.1.0 [110/20] via 20.1.1.3, 00:23:00, FastEthernet1/0
R3#sho ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is 10.1.1.2 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 10.1.1.2
1.0.0.0/24 is subnetted, 1 subnets
S 1.1.1.0 [1/0] via 12.1.1.1
3.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 3.3.3.0/24 is directly connected, Loopback0
L 3.3.3.3/32 is directly connected, Loopback0
5.0.0.0/32 is subnetted, 1 subnets
O 5.5.5.5 [110/2] via 20.1.1.5, 00:27:56, FastEthernet1/1
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.1.1.0/24 is directly connected, FastEthernet1/0
L 10.1.1.3/32 is directly connected, FastEthernet1/0
20.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 20.1.1.0/24 is directly connected, FastEthernet1/1
L 20.1.1.3/32 is directly connected, FastEthernet1/1
测试一下设备切换:
可以将R3重启reload或者将接口shutdown
R3(config)#int f1/0
R3(config-if)#shu
R4#
*Apr 23 19:21:43.491: %HSRP-5-STATECHANGE: FastEthernet1/0 Grp 1 state Standby -> Active
R1#ping 5.5.5.5 so 1.1.1.1 repeat 1000
Type escape sequence to abort.
Sending 1000, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!!!!!...........!!!!!!!!!!!.!!!!!!.
Success rate is 66 percent (26/39), round-trip min/avg/max = 236/432/644 ms